Wearing my other hat for SentinelOne, I recently wrote about PowerShell and some of the ways it can be used by malware authors. Along the way, I discovered two things I hadn’t previously known: there is a version of PowerShell that runs on macOS (surprise!), and the signed Microsoft installer for such litters the user’s Mac with multiple executables in privileged locations that are not themselves codesigned, and are therefore vulnerable to hijack by bad actors (shock!).
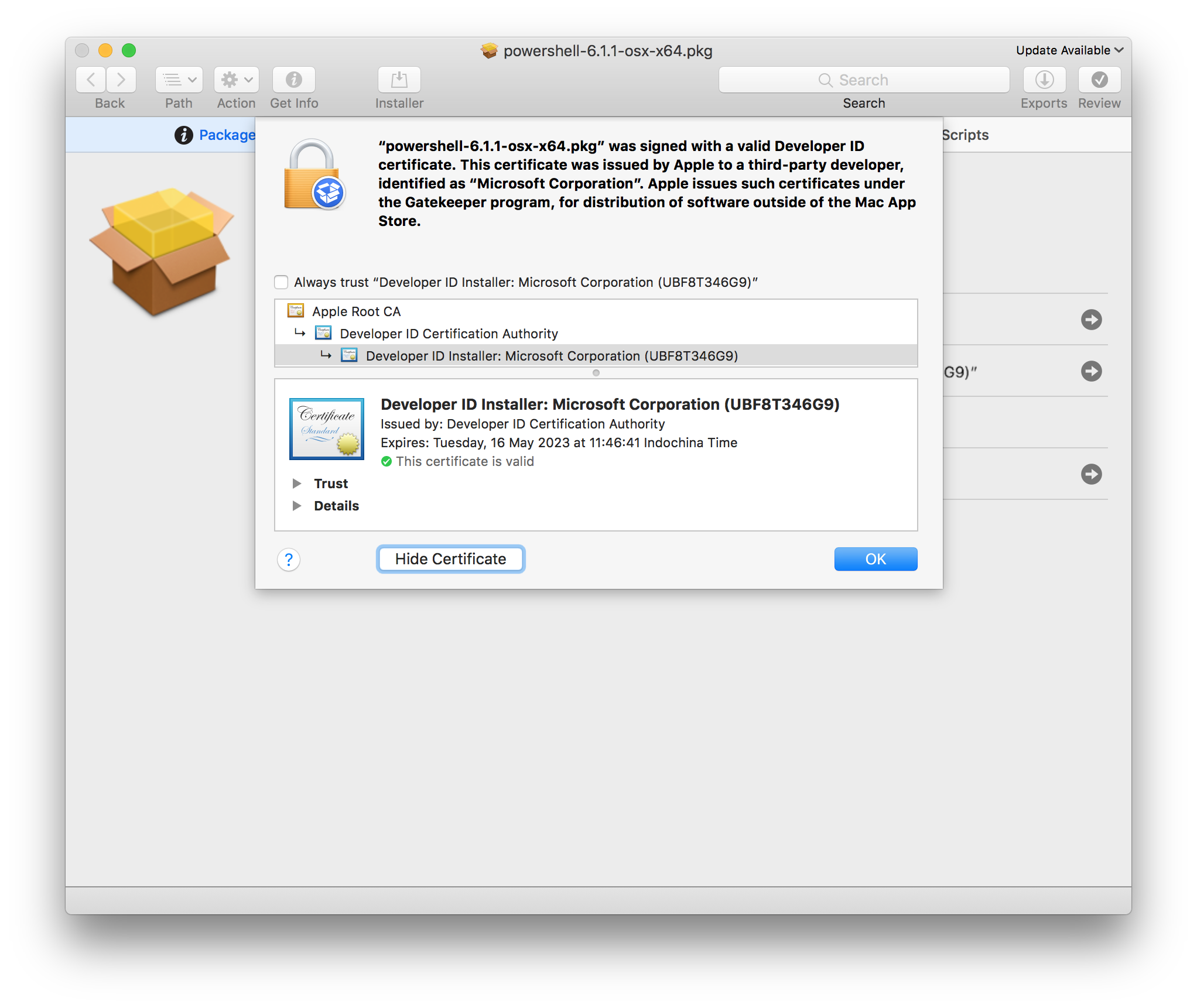
The PowerShell Core installer for macOS is a 54MB .pkg called powershell-6.1.1-osx-x64.tar.gz. Examining this with Suspicious Package reveals it is correctly signed with Microsoft’s developer certificate:
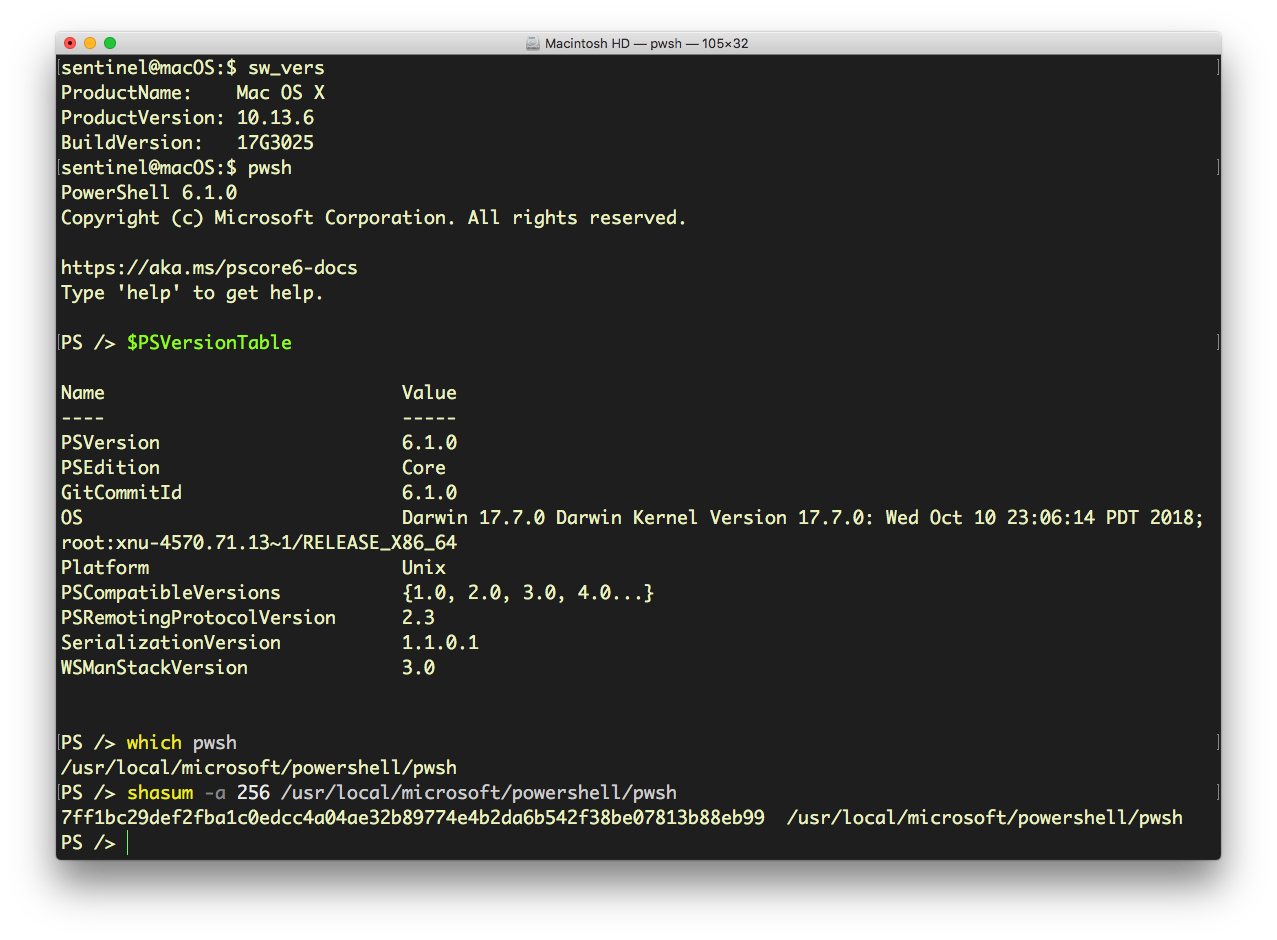
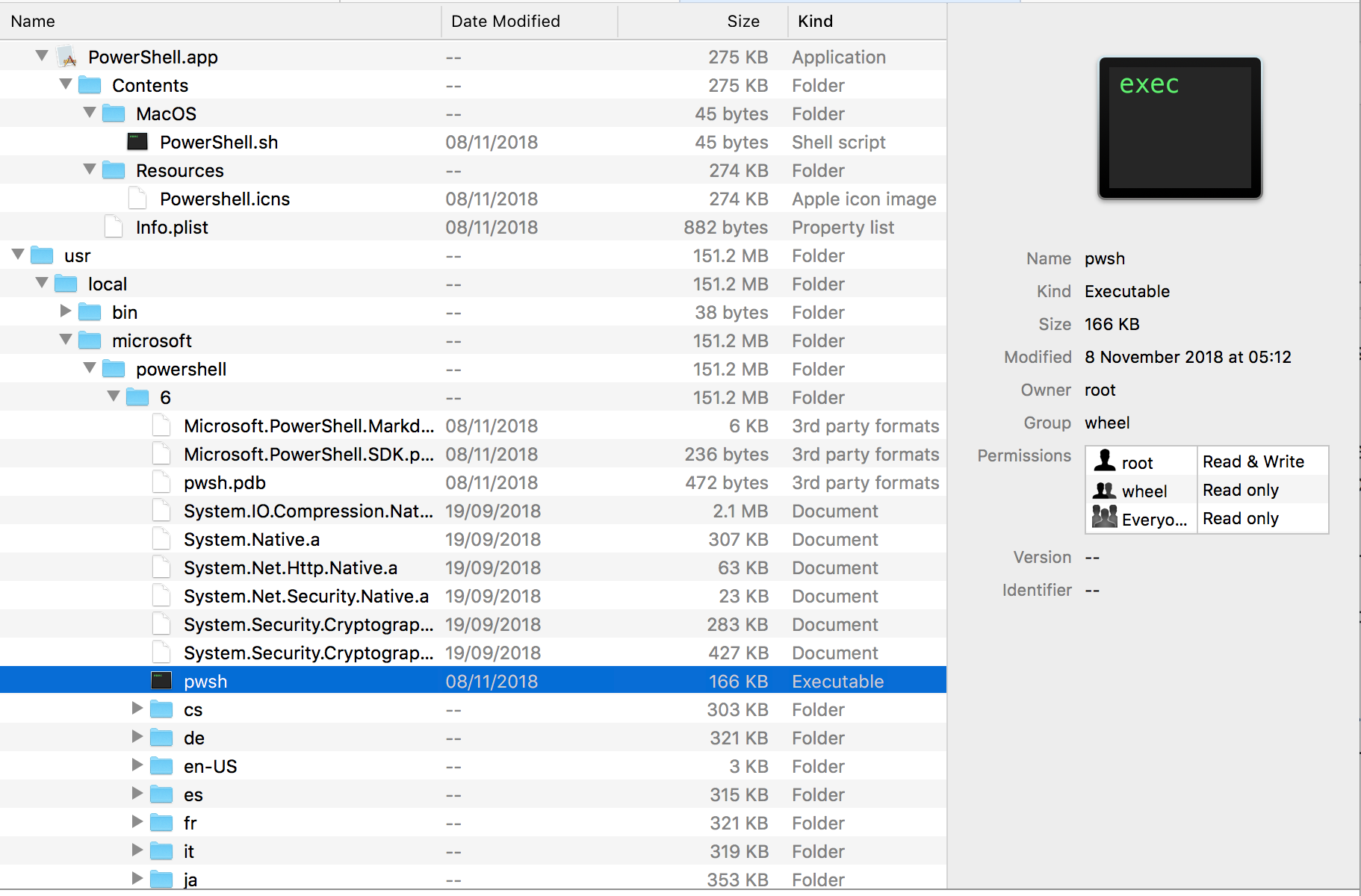
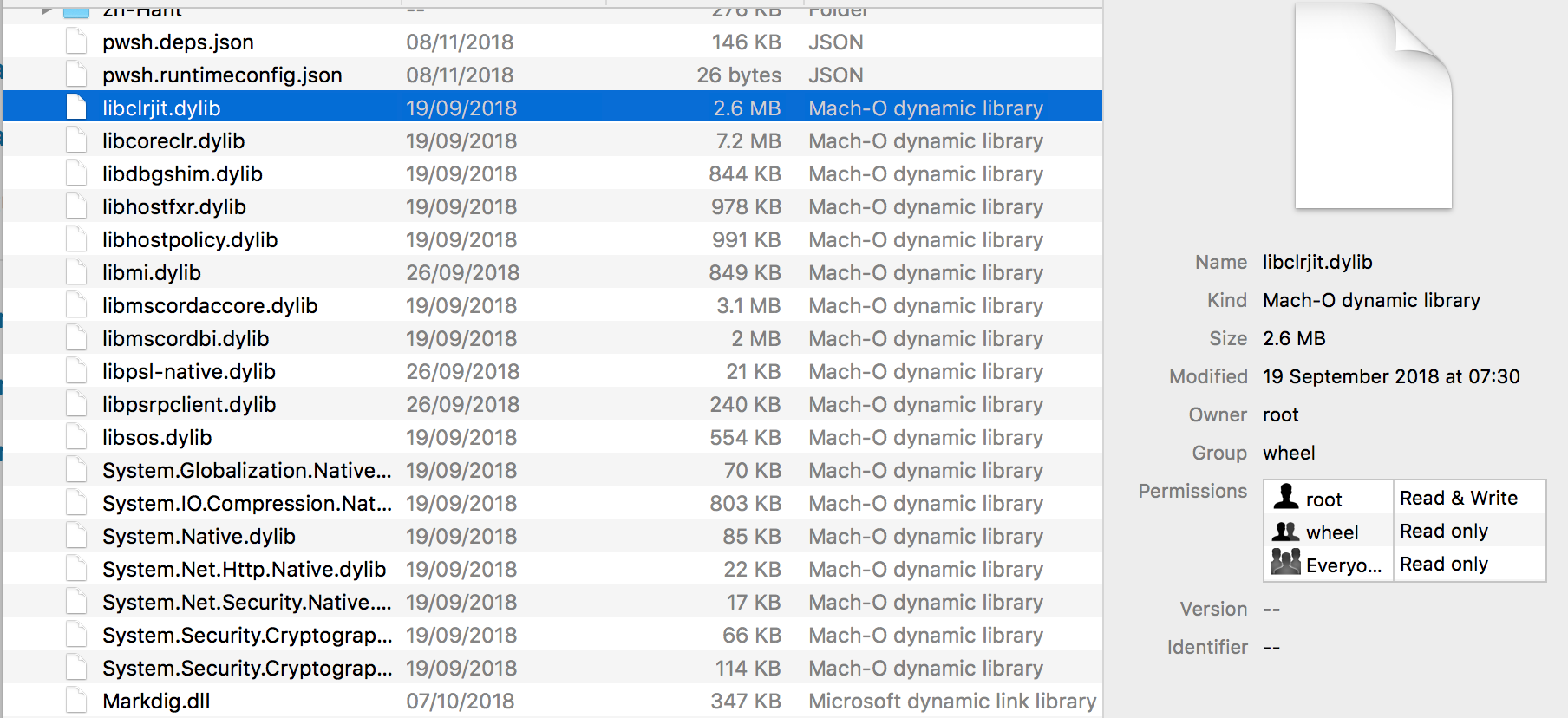
It installs 540 items on disk, including multiple Mach-O binaries in /usr/local/microsoft/powershell/6 directory, among which is the pwsh executable itself.
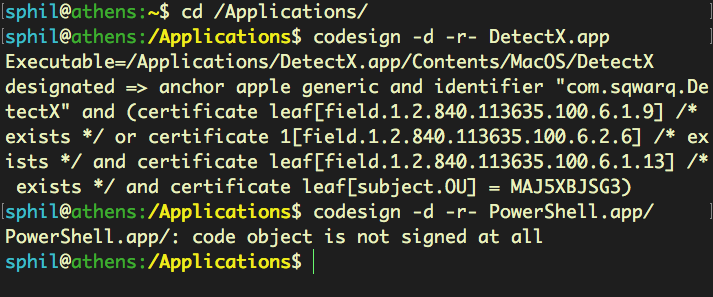
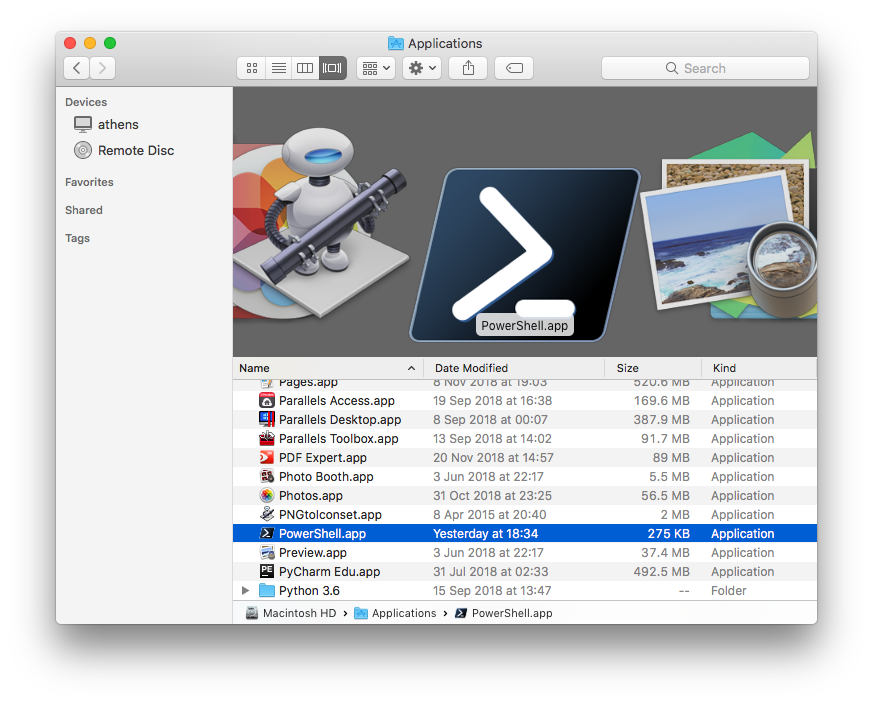
The installer also drops an application bundle in the Applications directory, which is also unsigned, and unquarantined, the latter meaning that regardless of the user’s Gatekeeper settings, this app will launch without triggering Apple’s perfunctory security checks.
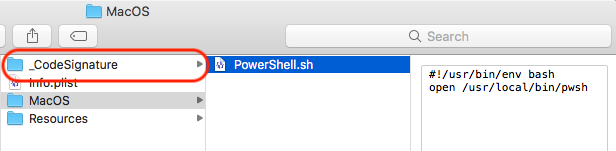
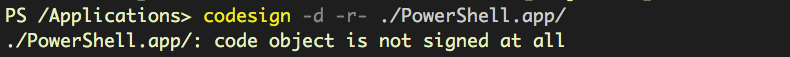
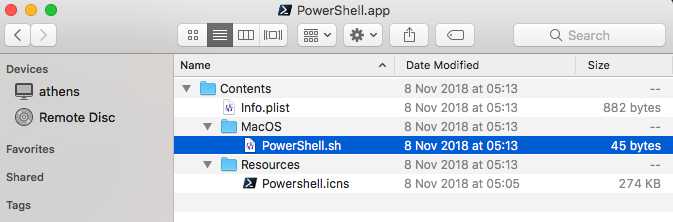
As the images below show, the bundle contains no _CodeSignature folder, and is a “barebones” wrapper for an icon, Info.plist and a Bash script that launches the pwsh command line tool in the Terminal.
Without being signed, these objects could easily be replaced by impostors with malicious behaviour and the user would have no idea. The dangers of code hijacking are well-known, and there’s really no excuse for Microsoft leaving macOS users vulnerable by installing executables with privileged permissions and no check as to their validity.
What can you do?
Users of PowerShell Core on macOS could either sign the items themselves if they have a valid developer certificate, or in a pinch, run shasum checks against the binaries to ensure they haven’t been changed.